Meet the Army officer who’s become the accidental face of romance scams around the world
“As one account goes down, more pop up."

It was a Saturday in November when Deborah Colgate got a Facebook message from a man named Daniel Blackmon.
Colgate, 56, was recently separated and admittedly lonely, yet intrigued by Blackmon. He was handsome, kind, and a colonel in the U.S. Army. He asked about her family, what she did for work, if she had grandchildren. He told her how beautiful her smile was. They talked about their hobbies, and their interests, and within a few weeks, Blackmon started opening up to her. He said his wife had left him after trying to kill their son, Alvin. And because Blackmon said he was currently deployed, Alvin was living with a family friend in England. Meanwhile, Blackmon soon made it clear his feelings for Colgate were growing stronger: He wanted to be with her, he said. He wanted to marry her.
It wasn’t until Blackmon started asking Colgate for money that her daughter, Brandi, who worked at a bank at the time, felt something wasn’t right. Blackmon was telling Deborah that doctors had found tumors on his son’s stomach, and he desperately needed surgery. He said he couldn’t access his money because he was deployed, and asked Deborah if she could lend him a few thousand dollars.
But what Brandi found when she searched Daniel Blackmon wasn’t what she expected: the real Daniel Blackmon, an Army colonel in Oklahoma, was happily married with children.

She and her mother would soon learn they were two of hundreds, if not thousands of people who were being scammed by people using Blackmon’s identity. Most of the profiles used Blackmon’s full name, and photos he’d shared previously on Twitter, though some used only his photos and a different name. His selfies were their profile photos; they’d rip off pictures he’d posted online in uniform and share them with women they spoke with.
Blackmon — the real one — estimates there are hundreds of fake accounts using his name and photos across various social media sites since he was alerted to the first fake account under his name in 2014. If there’s an online dating website in the world, he said, he probably has accounts on it.
He’s far from the only service member whose likeness is used to scam unsuspecting people — typically women — into believing they’re in a friendship, or even romantic relationship, with the person behind the scam. The top U.S. general in Afghanistan once said officials had uncovered more than 700 fake profiles under his name. And others with high profiles, such as former Defense Secretary Jim Mattis and former Chairman of the Joint Chiefs Joseph Dunford, have reported similar impersonations. Military romance scams are so common in fact that the Army’s Criminal Investigation Division has an entire webpage dedicated to informing people on how to spot them and report them.
In a way, it’s not much different than other popular scams of the past, like the infamous “Nigerian prince” emails asking people for their bank information that still rake in hundreds of thousands of dollars a year, according to ADT Security Services. But military romance scams, in particular, expose the knowledge gap between American citizens and their military. Troops deployed overseas, for example, will always have access to their money. And even if for some strange reason they didn’t, would they really be asking a stranger to send them thousands?
But much like the Nigerian prince scam — or the scam robocalls urging people to extend a car warranty — the best way to fight them is to ensure everyone knows they’re a scam.
“We’ve just got to do our best to highlight it, and the more you highlight it the less chance they have,” Blackmon said of the scammers. “And they’ll move on to something else. But it isn’t going to be this one.”
‘They know I know who they are. Or at least that I’m watching.’
The story is almost always the same.
On the other end of the instant messenger window is a U.S. service member. They’re deployed on a secret mission, or maybe a United Nations peacekeeping mission, in a country such as Yemen, Syria or Iraq. They’re a widower, or divorced. They can’t access their money, despite clearly having access to Facebook or Instagram. They can’t talk to you on video, for security reasons.
The script is so familiar that the Army includes those “red flags” on its website about romance scams. Among those red flags are people using phrases like, “‘my love,’ ‘my darling,’ or any other affectionate term almost immediately.”
“[T]hey claim to be a U.S. Army soldier; however, their English and grammar do not match that of someone born and raised in the United States,” the Army’s site says.
That’s how it was for Connie Poindexter, who shared messages she received from “Daniel Blackmon” with Task & Purpose. The person, who said he was on a mission in Yemen, repeatedly called her “my Queen,” and asked if she could tell him “what you like and what you dislike” because he didn’t “want to hurt you or talk to you in the way you will feel hurt.”

“My ex hurt me but I feel strong now and I only focus on my job,” read one message to Poindexter sent in January. “You’re just like God sent to me because I don’t have time to talk to someone since I experience [sic] heart break.”
Poindexter, who is married and told the fake accounts as much repeatedly, said she was first contacted by someone named Daniel Blackmon in October 2021. Since then, she has been contacted by at least 15 accounts with the same name.
“Every single one of them almost told me the same story about losing their mother at seven, their dad at 13, their first date was the same, their first love was the same, their favorite color was the same — white for a pure heart, and red for love — they all asked me the same questions,” Poindexter said.
The conversation eventually would progress to the crux of the scam; Poindexter said for some, the story would be that there had been an attack on their campsite “and some of the men died,” and that the remaining troops were instructed to send their valuables back to the U.S. to a beneficiary.
“So they wanted me to be their beneficiary,” Poindexter said.
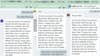
Other bogus stories included that their “data was running out,” and they needed a $300 gift card. Two other people told her they were approved for retirement, but they’d “have to wait two days to find out what their retirement pay was.” (Military retirees are well aware of their potential retirement pay since the Pentagon has outlined clear guidelines.)
“I’m like, that’s really weird, because that’s not how it works,” Poindexter said. “But they announced the retirement pay of $600,000, but in order to do that they have to have an account for it to be transferred into. So they need my bank information so they can transfer the money in.”
In November, Poindexter decided to do some digging of her own. She searched Daniel Blackmon online and sent him a message on Twitter, telling him that she had “Daniel Blackmons pretending to be him.” She confronted the fake Blackmons, telling them she’d found the real person and she knew they were imposters. They adamantly denied it, she said, even going so far as to say the real Blackmon was actually the imposter.
Notably, as soon as the real Blackmon posted a photo of himself on Twitter, the fake Blackmons would send her the same photo soon after, claiming it was them.
The real Blackmon is “fairly open on Twitter,” he said, and he knows that’s where most of what the scammers use comes from. But in the early days of the scam, around 2014 and later, he realized they were lifting photos of him and his family off of Facebook. He didn’t have strict privacy settings at the time. His life “was an open book.”

Since then, he’s locked down his Facebook and Instagram accounts to only allow people he knows personally to follow him. And while his Instagram account is private, the bio on his page is public.
“I’m the real Daniel Blackmon,” it says. “I don’t follow if I don’t know you. I am only public on Twitter. I’m happily married, not deployed and won’t ask for $$.”
He’s even noticed that some of the fake accounts are blocking his real account on Instagram, possibly in an effort to keep him from seeing them using his identity and reporting them. “They know I know who they are,” he said. “Or that I’m at least watching.”
To see through the scams, it’s critical to have an understanding of how the military works, Blackmon said. At the very least, people need to know that service members who are deployed don’t have a problem accessing their money. “We all can get access to our banks,” he said. “If we can get on a cell phone, we can get access to our banks.”
If people know that, then perhaps it will disrupt the idea behind the scam that troops are stuck without money, can’t deposit their paycheck, or need help getting funds to a sick family member. Though Colgate and Poindexter caught on quickly and never sent money to the imposters, others haven’t been so lucky.
Poindexter recalled finding one woman on Instagram who was caught in a scam with a “Daniel Blackmon,” and was heartbroken when she learned the truth. She “literally fell in love” with him, Poindexter said.
In 2014, the niece of another victim told Blackmon she believed someone was using his identity and speaking to her aunt, he recalled. When he went on Facebook, he found that she’d created a photo collage of sorts with their separate photos.
His photos were used, but with a different name. On Facebook, Blackmon could see them comment back and forth to one another, saying “my love, and my sweet, and all this pretty cheesy stuff that would never come out of my mouth,” he said. The woman who had reached out to him said her aunt had sent this man a couple thousand dollars already, and she was concerned.
Blackmon said he sent the scammed woman a message on Facebook, telling her someone was using his pictures to scam her. She didn’t believe him. It wasn’t until Blackmon took a photo with a newspaper, pointing at the day’s date, for her to realize what was happening.
Since then, he has tried to help other women who are getting scammed in the same way, some of whom believe him, while others don’t.
“They’ve got a good scam,” Blackmon said. “It’s been going on for years.”
‘As one account goes down, more pop up’
One of the first profiles that appears when you search “Daniel Blackmon” on Facebook is a fake account. It says he’s divorced, studied at Upper Iowa University, and lives in Virginia.
Scroll down the list of Blackmons, and you’ll find another, which shows the exact same details. The account looked relatively new when viewed on Feb. 23, having posted a profile photo that morning. But reporting them will amount to almost nothing, Blackmon said.
“If I go and report this, which I’ve done, I’ll get a report in 12 hours that says this doesn’t violate community standards,” he said. Facebook did not respond to a request for comment.
Part of what makes it so difficult is likely the sheer volume of fake accounts on Facebook. In 2019, the company announced that in just three months it had removed 2.2 billion fake accounts from the site. It was a record-breaking number; in the previous quarter, Facebook had purged 1.2 billion accounts, and in the quarter before that, 694 million.
Another potential factor for why the accounts are difficult to get their arms around is the way they’re operated. According to Deborah Colgate, some of the accounts who reached out to her “only stayed for a day.” They would contact her, talk briefly, then try to move her to another platform and disappear from Facebook.
But it’s not just Facebook, and it’s not just Blackmon. Former Defense Secretary Ash Carter has been impersonated. Scammers have used the identities of Gen. Paul Nakasone, director of the National Security Agency and head of U.S. Cyber Command, and Gen. Stephon Lyons, formerly the head of U.S. Transportation Command, to pull off romance scams. And there’s at least one fake Tinder profile of Sgt. Maj. of the Army Michael Grinston out there. (An Army official confirmed Grinston has never used the popular dating platform.)
A screenshot of the fake profile obtained by Task & Purpose falsely claims Grinston is 40 years old and graduated from the U.S. Military Academy at West Point. The account’s bio says Grinston, who is in his 50s and happily married, is “A very Simple/single, and understanding man plus I can make you laugh though.”

It’s more than just a nuisance, Blackmon said, though it is certainly that. He said his wife “doesn’t even talk about it because it frustrates her so much” that the scammers pretend Blackmon is a widower. “You know, she’s been killed off … in multiple different ways.”
The scams may even be a national security issue. While most of the accounts are just after money, what if they began using the accounts to try to gain access to information?
“Think how easy it would be, to be honest, for somebody to take all of my stuff that they currently have, make a fake profile in some form or fashion, and then completely discredit the United States Army?” Blackmon said. “Just in the world we’re in today, it wouldn’t take much for somebody to create a fake profile of me and then get on there and start spouting out stuff that is either inaccurate or not in line with Army values. And it would take on a life of its own.”
While the Army does try keep a handle on fake accounts, it’s mostly up to the individual media sites. Army Criminal Investigation Division spokesman Jeffrey Castro said the division “does have relationships with social media and dating sites.” But CID investigates felony-level crime, he said, and imposter accounts don’t necessarily reach that level.
“It’s important to note that imposter accounts by themselves are not criminal and don’t always violate the media providers terms of service,” he said. “That is up to the individual provider to determine.”
Over the past year, Castro said, CID has received more than 30,000 notifications of imposter accounts. “As one account goes down, more pop up creating a never ending cycle.”
The overwhelming sense of how many kinds of accounts like this are out there is of course part of the problem, Blackmon said. “It’s whac-a-mole.”
What’s new on Task & Purpose
- The ‘Ghost of Kyiv’ is the first urban legend of Russia’s invasion of Ukraine
- Man calls into public radio with tips on how to make Molotov cocktails in Ukraine
- ‘Russian warship, go f–k yourself’ — Ukrainian troops make heroic last stand on Black Sea island
- The Navy is moving ahead with court-martial of a sailor accused of torching a $3 billion warship
- Military nuclear experts explain the actual danger of troops battling in the shadow of Chernobyl
- Here’s what those mysterious white ‘Z’ markings on Russian military equipment may mean
Want to write for Task & Purpose? Click here. Or check out the latest stories on our homepage.
